Email-Worm.Win32.Merond.a worm spreads as an attachment to infected emails and also via file-sharing networks and removable media. The worm itself is a Windows PE EXE file. The worm’s executable file can vary between 150KB to 400KB in size.
The worm copies its executable file to the Windows system directory:
%System%\javaupd.exe
%System%\javaqs.exe
Propagation via email
The worm harvests email addresses from files with the following extensions:
txt, htm ,shtl ,php, as,p dbx ,dbh, wab,It also harvest addresses from the victim machine’s address book.
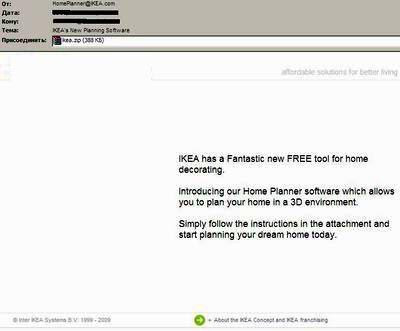
It looks like this
The zip archive contains a file called "ikea" which will have one of the extensions listed below:
.zip .rar .cab .txt .reg .msi .htm .html .bat .cmd .pif .scr .mov .mp3 .wav
It also has an .exe extension after the first extension.
If your computer does not have an up-to-date antivirus, or does not have an antivirus solution at all, follow the instructions below to delete the malicious program:
- Use Task Manager to terminate the malicious program’s process.
- Delete the original worm file (the location will depend on how the program originally penetrated the victim machine).
- Delete the following system registry parameters: [HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"Kaspersky Email Security" = "%System%\javaupd.exe"
[HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run]
"Java update" = "%System%\javaqs.exe"
[HKCU\Software\Microsoft\Windows\CurrentVersion\Run]
"Java update" = "%System%\javaqs.exe"
[HKLM\SOFTWARE\Microsoft\Active Setup\Installed Components\{1A2K5H58-65CP-B7PP-F600-
3023OJX71M20}]
"StubPath" = "%System%\javaqs.exe" - Delete the following files:
%System%\javaupd.exe
%System%\javaqs.exe - Delete the files shown below from all removable storage media:
:\autorun.inf :\redmond.exe X is the name of the removable disk
- Update your antivirus databases and perform a full scan of the computer
No comments:
Post a Comment