Cybercriminals are putting forth every effort to make malware difficult to detect. Successfully, I might add. Ever optimistic, I thought I would have a go at providing information on how to make their job a little tougher.
Knowing exactly what is running on a computer is paramount to learning what shouldn't be. Creating a reference baseline is the best way I've found to accomplish this. Let's look at three applications that do just that.
Microsoft Process Explorer (formerly Sysinternals)
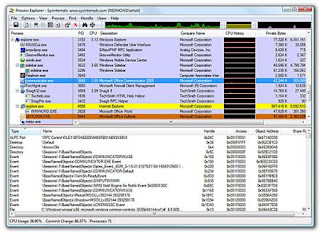
Process Explorer provides an excellent way to determine what processes are running on a computer. It also describes the function of each process. More important, you can use Process Explorer to create a baseline of the running processes used by the computer when it's operating correctly. If for some reason the computer starts behaving poorly, run Process Explorer again and compare the scans. Any differences will be good places to start looking for malware.
Trend Micro's HiJackThis

HiJackThis is Process Explorer on steroids, making the application somewhat daunting to those of us not completely familiar with operating systems. Still, running HiJackThis before having malware problems creates a great reference baseline, making it easy to spot changes. If it's too late to run a baseline scan, do not fear. Several Web sites offer online applications that will automatically analyze the log file from HiJackThis, pointing out possible conflicts. Two that I use are HiJackThis.de Security and NetworkTechs.com. If you would rather have trained experts help, I would recommend WindowSecurity.com's HiJackThis forum.
Kaspersky's GetSystemInfo
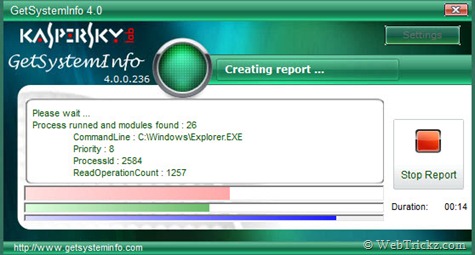
Kaspersky has an application similar to HiJackThis called GetSystemInfo. I like the fact that Kaspersky has an online parser. Just upload the log file and the parser will point out any disparities. GetSystemInfo, like the other scanners, is a good way to keep track of what's on the computer, and if need be, it can help find any malware that happens to sneak in. Be careful: As I alluded to earlier, removing processes suggested by the scanners is not for the faint of heart. It requires in-depth knowledge of operating systems or being able to compare before and after scans.
Anti-malware includes any program that combats malware, whether it’s real-time protection or detection and removal of existing malware. Vulnerability scanners proactively detect vulnerabilities so that malware can't gain a foothold. I'd rather update applications than chase malware any day.
Microsoft Baseline Security Analyzer
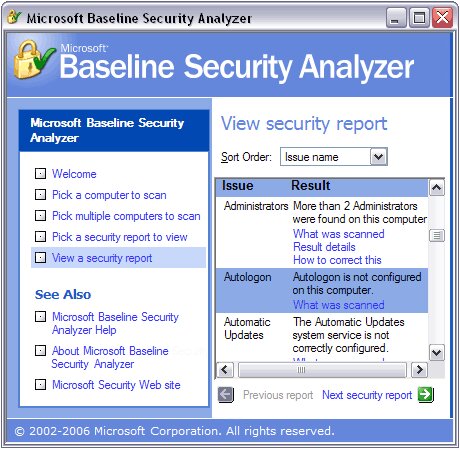
Microsoft Baseline Security Analyzer (MBSA) is a vulnerability scanner that detects insecure configuration settings and checks all installed Microsoft products for missing security updates. I recommend using MBSA when upper management needs convincing. Making a case for needing a vulnerability scanner is sometimes easier if the product is from the OEM.
Secunia inspection scanners

Secunia's scanners are similar to MBSA when it comes to Microsoft products. But unlike MBSA, Secunia products also scan hundreds of third-party applications, which gives Secunia a distinct advantage. All the Secunia scanners, online and client-side, have an intuitive way of determining what is wrong and how to rectify it. They usually offer a link to the application's Web page, where the update can be downloaded.
Antivirus programs
Lately, antivirus software is getting little respect. Like everyone, I get frustrated when my antivirus program misses malcode that other scanners mange to find. Still, I would not run a computer without antivirus. It's too risky. I subscribe to the layered approach when it comes to security.Choosing the correct antivirus application is personal. Comments come fast and furious when someone asks TechRepublic members which one is the best. A majority feel that any of the free versions are fine for nonbusiness use. I use Avira or Comodo on Windows machines.
10+Best Free Genuine Antivirus Softwares for Home
Anti-malware enforcers
The next class of anti-malware is capable of both detecting and removing malware. I'm sure you are wondering why not just use these from the start. I wish it was that simple. Scanners use signature files and heuristics to detect malware. Malware developers know all about each and can morph their code, which then nullifies signature files and confuses heuristics. That's why malware scanners aren't the cure-all answer. Maybe someday. More caution: I want to emphasize that you need to be careful when picking malware scanners. The bad guys like to disguise malware (antivirus 2009) as a malware scanner, claiming it will solve all your problems. All four of the scanners I have chosen are recommended by experts.
Microsoft's Malicious Software Removal Tool

Malicious Software Removal Tool (MSRT) is a good general malware removal tool, simply because Microsoft should know whether the scanned code is theirs or not. Three things I like about MSRT are: • The scan and removal process is automated. • Windows Update keeps the signature file database current automatically. • It has the advantage of being an OEM product, thus it's less intrusive and more likely to be accepted by management.
SUPERAntiSpyware

SUPERAntiSpyware is another general purpose scanner that does a good job of detecting and removing most malware. I have used it on several occasions and found it to be more than adequate. A number of TechRepublic members have mentioned to me that SUPERAntiSpyware was the only scanner they found capable of completely removing antivirus 2009 (malware).
Malwarebyte's Anti-Malware

Malwarebytes Anti-Malware (MBAM) malware scanner was the most successful of the four I tested. I was first introduced to it by world-renowned malware expert Dr. Jose Nazario of Arbor Networks. For a detailed explanation of how MBAM works, refer to my post Malware scanners: MBAM is best of breed. Still, MBAM does not catch everything. As I pointed out in the MBAM article, it misses some of the more sophisticated malware, especially rootkits. When that happens, I turn to the next malware scanner.
GMER
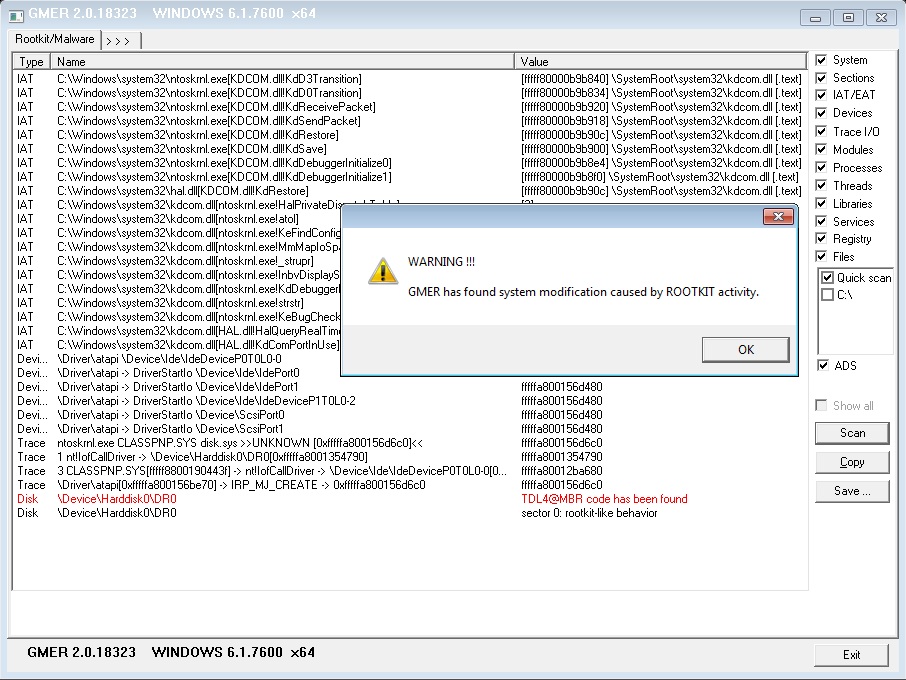
In Rootkits: Is removing them even possible?, I explained why it's hard to find rootkit malware. Fortunately, GMER is one of the best when it comes to detecting and removing rootkits -- enough so that it's recommended by Dr. Nazario.








